What is Remote Desktop Protocol (RDP)?
RDP stands for Remote Desktop Protocol. It’s an proprietary protocol developed by Microsoft that allows a user to connect to and control another computer over a network connection. With RDP, you can access and use the desktop environment and applications of a remote computer as if you were physically present at that computer. RDP is commonly used for remote administration, technical support, and accessing files or resources on remote computers in a networked environment.

How Does RDP Work?
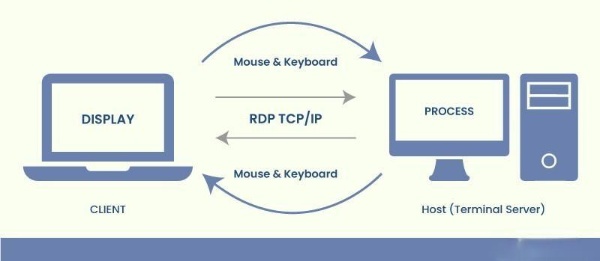
- Remote Desktop Protocol (RDP) works by allowing a user to establish a connection between two computers over a network. Here’s a simplified overview of how it works:
- Initiating the Connection: The user starts by initiating an RDP session from their local computer (referred to as the client) to a remote computer (referred to as the host) that they want to access.
- Handshake and Authentication: The client and host computers communicate to negotiate the connection parameters and authenticate the user’s credentials. This typically involves verifying the user’s username and password or using other authentication methods like smart cards.
- Establishing the Connection: Once authentication is successful, the client and host establish a connection using the RDP protocol. This connection is typically encrypted to ensure security during data transmission.
- User Interaction: The user can now interact with the remote desktop environment as if they were physically present at the remote computer. They can open applications, access files, and perform tasks just like they would on a local computer.
- Data Transmission: Any user input, such as keyboard and mouse actions, are transmitted from the client to the host over the RDP connection. Similarly, the host sends screen updates and other data back to the client to display the remote desktop environment on the user’s local screen.
- Session Termination: When the user is done with the remote session, they can choose to disconnect or log off. This terminates the RDP connection between the client and the host.
Pros and Cons of RDP
| Pros | Cons |
| Remote access from anywhere | Bandwidth dependency |
| Centralized management | Potential security risks |
| Resource efficiency | Limited platform support |
| Security features | Lack of features for some use cases |
| Integration with Windows ecosystem | Concurrency limitations (depending on Windows edition) |
Remote Desktop Protocol (RDP) is Safe for Browsing .?
Remote Desktop Protocol (RDP) itself is not used for browsing the internet. Instead, it’s a protocol primarily used for remote access and management of computers over a network. However, regarding safety, RDP can be secure if configured properly with strong authentication mechanisms, encryption, and proper network security measures.
That said, using RDP for remote access does come with security considerations. If not configured securely, RDP can be vulnerable to attacks such as brute force password guessing, man-in-the-middle attacks, and exploitation of known vulnerabilities.
consider below some tips to ensure safe usage of RDP:
- Use Strong Authentication: Require users to use complex passwords and consider implementing multi-factor authentication for an extra layer of security.
- Enable Network Level Authentication (NLA): NLA requires users to authenticate before establishing a session, reducing the risk of unauthorized access.
- Encrypt RDP Traffic: Ensure that RDP connections are encrypted using strong encryption protocols like TLS (Transport Layer Security) to protect data during transmission.
- Limit Access: Restrict RDP access to only authorized users and IP addresses, and consider using VPNs or firewalls to further control access.
- Keep Software Updated: Regularly update RDP client and server software to patch known vulnerabilities and enhance security.
- Monitor for Suspicious Activity: Implement monitoring and logging mechanisms to detect and respond to any suspicious or unauthorized access attempts.
VPN vs RDP which one is Best
Comparing Remote Desktop Protocol (RDP) and Virtual Private Network (VPN) is a bit like comparing apples and oranges because they serve different purposes. However, I can highlight their key differences and use cases to help you understand which one might be best for your needs:
Remote Desktop Protocol (RDP):
- Purpose: RDP is primarily used for remote access and control of computers or virtual desktops. It allows users to connect to a remote computer’s desktop environment and interact with it as if they were physically present.
- Use Case: RDP is ideal for scenarios where users need direct access to specific applications or resources on a remote computer, such as technical support, remote administration, or accessing proprietary software.
Virtual Private Network (VPN):
- Purpose: VPN creates a secure, encrypted connection between a user’s device and a private network over the internet. It enables users to access resources on the private network securely from remote locations.
- Use Case: VPN is commonly used to establish secure connections to corporate networks, access internal resources (like files, servers, or databases) securely from remote locations, and ensure privacy and security while browsing the internet on public Wi-Fi networks.
When deciding between RDP and VPN, consider the following factors:
- Nature of Access: If you need direct access to a specific computer or desktop environment, RDP is more appropriate. If you need access to resources on a private network from a remote location, VPN is the way to go.
- Security: Both RDP and VPN can be secure when configured properly, but VPN is generally considered more secure for remote access to network resources as it encrypts all traffic between the user’s device and the private network.
- Ease of Use: RDP may be more straightforward for accessing a remote desktop environment, while VPN might require additional configuration and setup.
- Scalability: VPN is often more scalable for providing remote access to multiple users across different locations, whereas RDP may be more suitable for one-to-one remote access scenarios.
Top 10 ways to Ultimately using the RDP
- Ensure Security: Implement strong authentication methods, such as complex passwords or multi-factor authentication, to secure RDP access. Enable Network Level Authentication (NLA) to require authentication before establishing a session. Additionally, keep your RDP client and server software updated to patch known vulnerabilities.
- Optimize Performance: Configure RDP settings to optimize performance based on your network connection and remote desktop requirements.
- Use Remote Resources: Take advantage of RDP’s ability to access remote resources. Instead of accessing the entire desktop, consider launching specific applications or files remotely to save bandwidth and streamline your workflow.
- Customize Experience: Customize your RDP experience to suit your preferences.
- Enable Remote Printing: If you need to print documents from a remote computer, configure RDP to enable remote printing. This allows you to print to your local printer from the remote desktop environment seamlessly.
- Implement RemoteFX: If you require high-quality graphics or multimedia capabilities in your remote sessions, consider using RemoteFX, a set of RDP technologies designed to enhance graphics and media performance over RDP connections.
- Set Up Remote Gateway: If you need to access remote desktops from outside your network, set up a Remote Desktop Gateway (RD Gateway) to securely proxy RDP connections over the internet.
- Monitor Sessions: Implement monitoring and logging mechanisms to track RDP sessions for auditing and troubleshooting purposes.
- Consider RemoteFX USB Redirection: If you need to access USB devices connected to your local computer from a remote session, consider enabling RemoteFX USB redirection. This allows you to use USB devices such as flash drives or external hard drives within the remote desktop environment.
- Educate Users: Provide training and guidelines to users on how to use RDP securely and effectively. This includes best practices for connecting to remote desktops, avoiding common pitfalls, and recognizing potential security threats.